Did you know your most significant cyber security threats aren’t on the outside? Risky acts can come from anyone who has access to your network or information — including employees, contractors, suppliers, and partners. This can even mean inadvertent actions like an employee clicking a phishing link in an email.
So, how can you protect your company, your customers, and your data? Keep reading for a list of cyber security threats and ways to safeguard your business.
What Is Cyber Security Risk?
Your cybersecurity risk level is the likelihood a cyberattack will damage your organization’s assets and disrupt its ability to operate. In addition, it’s the chance a threat will exploit an existing vulnerability or find a new one. This might include the following scenarios.
- Data loss
- System disruption
- Reputation damage
Don’t let a cyber security threat disrupt your business or ruin your reputation!
Call TCS today to discuss your IT security needs.
Call 336.804.8449
3 Types of Inside Cybersecurity Threats and Vulnerabilities
“The idea that security starts and ends with the purchase of a prepackaged firewall is simply misguided.”
– Art Wittmann
Insider threats are not limited to malicious individuals. They also include those who unintentionally put their company at risk by failing to follow proper online security protocols and procedures.
Studies have shown 71% of all cyberattacks are due to human error — and 28% of those errors were unintentional! Use these tips to mitigate the risks of three common cybersecurity threats.
Protect Your Team from Phishing Emails
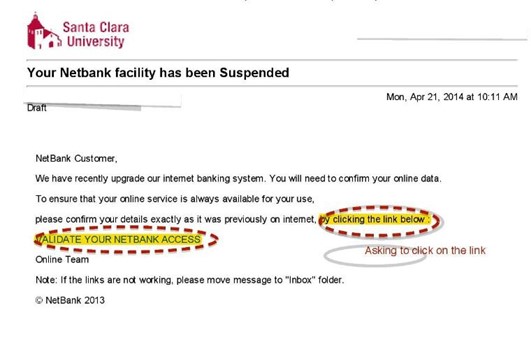
Phishing emails convince a user to reveal personal, financial or company information. Often carried out by email, a phishing scam may look like legitimate communication from your company’s HR, IT department, or even a boss — complete with a logo and email signature. However, the sender will ask the recipient to click on a link and enter sensitive data, such as passwords and account numbers.
Do these three things to protect your employees from phishing scams.
- Teach employees about phishing scams and how they work. See the example below.
- Warn employees about phishing emails that appear to come from your company or another trusted source (e.g., banks, credit card companies, lending institutions, etc.).
- Encourage employees not to click on links in suspicious emails or open attachments without first checking with IT or security personnel.
Beware of Social Engineering
Social engineering is a form of psychological manipulation that aims to trick people into giving up confidential information. It’s easy to understand how people fall victim to it — social engineers use sublet methods, most of which are hard to detect. For example, they may pretend they’re calling from an organization your company works with and trusts. Or they may pose as an IT professional and tell one of your employees about an issue with their account and ask for information to fix the problem.
Here are three ways to protect your business from social engineering cybersecurity threats:
- Train employees to recognize fraudulent emails, phone calls, and other communication attempts. Give them a clear understanding of personal information they should never share with anyone outside the company.
- Train employees to spot potential cyber safety concerns and report them to IT immediately.
- Use technology tools like multi-factor authentication (MFA) for sensitive applications such as email and VPN.
Don’t Underestimate the Risks of Unsecured, Lost, or Stolen Devices
One of the most basic but critical risks your company faces is unsecured devices, such as phones or laptops. In addition, lost or stolen devices pose a significant risk to your business. To help protect your company against these threats like ransomware, take these five precautions:
- Require passwords to be at least 12 characters.
- Use multi-factor authentication (MFA).
- Conduct risk and vulnerability assessments to identify weaknesses in your current defenses, either in house or with the assistance of your IT company.
- Create security policies to address proper device usage and disposal procedures.
- Enlist your IT company to provide regular employee training.
TCS Can Help You Prevent Cybersecurity Threats and Reduce Downtime
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
– Stephane Nappo
Do you need an IT partner to advise and consult on best practices to avoid a cybersecurity threat? Then, consider TCS your expert guide in all things IT. Don’t leave your security or reputation to chance!
Our support is local and prompt. When you call, you get a person, not a menu.